Privacy in Decentralized Physical Infrastructure Networks
Exploring the promise of one of blockchain's most tangible applications, DePIN.
The DePIN Landscape
The rise of decentralized physical infrastructure networks (DePIN) represents one of the most promising uses of blockchain. Unlike digital-only applications, DePINs connect the onchain and physical worlds, creating user-fueled networks of sensors, devices, and infrastructure.
DePINs span compute, telecomm, energy, storage, mobility, robotics, and more, with projects like Helium (wireless), Hivemapper (mapping), and Weatherflow (data) proving that crypto incentives can mobilize a distributed group of providers to deliver essential services.
Bootstrapping a network is one thing, but capturing the demand side has always been the question. Recent wins suggest the tide is turning: Hivemapper is selling real data to enterprise customers, some AI companies are using distributed compute alongside AWS, and Helium is collaborating with T-Mobile.
With the broader DePIN market projected to exceed $3.5 billion by 2028, the infrastructure is incrementally proving its worth. There's just one catch: as these networks mature, they must fully transition from speculative bootstrapping subsidies to economic value creation. They must also deal with the issue of privacy.
The Privacy Problem
DePIN faces the critical but often overlooked issue of data privacy. As these networks expand and create increasingly large datasets, they also introduce risks and, in some cases, barriers to realizing their full potential. By design, DePINs collect and parse real-world data. How this works is case-dependent, but with physical devices in play, it can often take forms like:
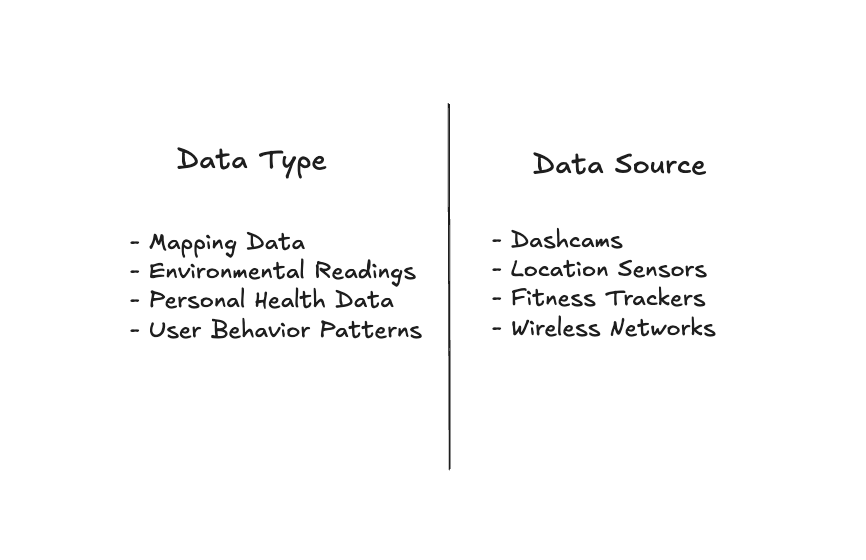
DePINs operate on a transparent Web3 architecture, many, for instance, on Solana, which means payment-related transactions are entirely visible onchain. Apart from payments, collected data and user data are often stored in a centralized database and are sometimes presented on websites or accessible via third-party explorers. This introduces significant trust requirements and vulnerabilities.
The implications are numerous. For example, hotspot earnings can compromise identity or activity patterns. A map contributor's metadata can be used to reveal their vehicle or location. Contextual user data can be fed to an AI model for training without any privacy guarantee (or compensation). Or an old-fashioned database leak can expose any number of details. What seems benign can become personally identifiable or exploitable through access and correlation techniques.
DePIN Privacy Solutions
Essentially all DePIN projects face a common challenge: balancing privacy with performance and security. There is a wide range of solutions for addressing the privacy aspect, including anonymizing provider data and implementing things like device diversity weighting, which prioritizes contributions from diverse sources to minimize location inference risks.
The other approaches fall into a few buckets. Some projects focus on data minimization - anonymizing providers, using approximate coordinates instead of precise locations, or claiming to store no PII at all. Others lean on things like client-side encryption, differential privacy, zero-knowledge proofs, or variants of zkTLS for validation without exposure.
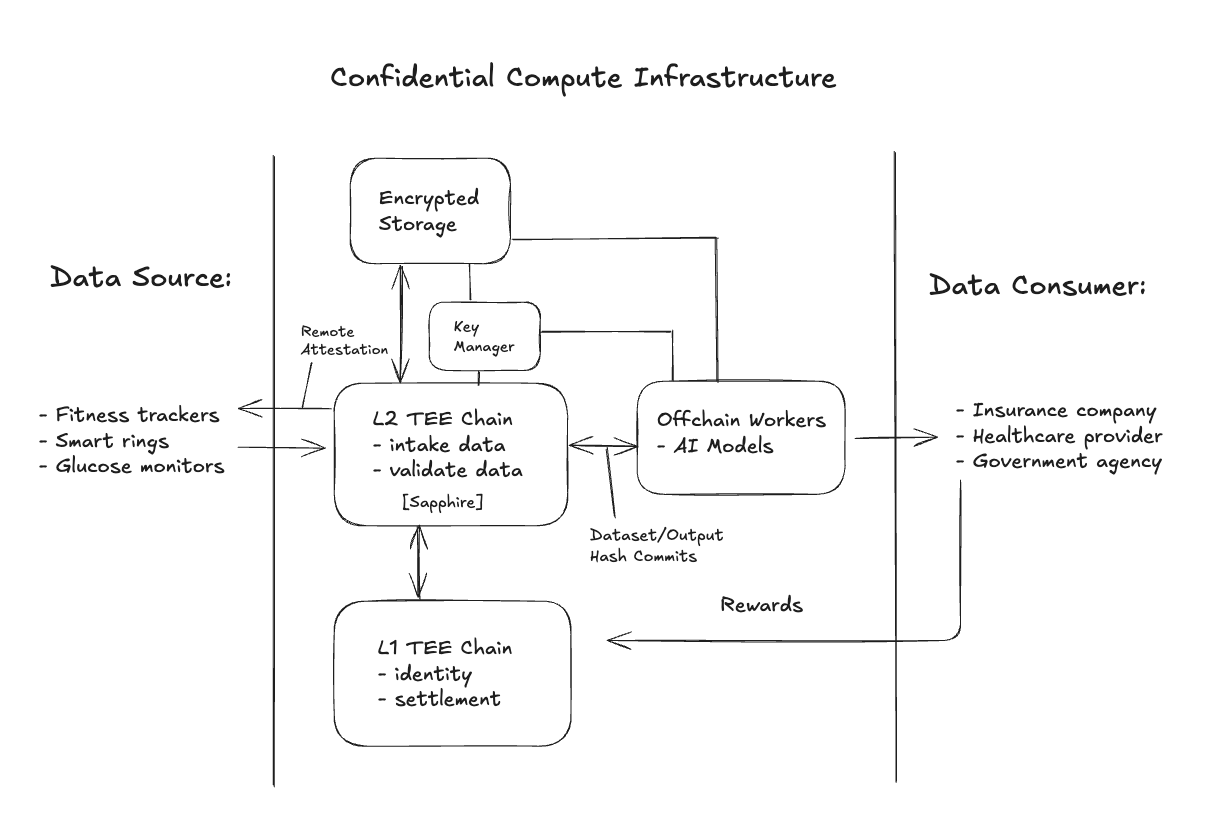
Another increasingly popular solution is confidential computing. Confidential computing technologies use hardware-based trusted execution environments (TEEs) to process data in secure enclaves that isolate code/data such that even the operator can't see what's happening inside the secure environment. This presents opportunities on two distinct but complementary fronts.
First, certain DePINs can include TEEs as a core service, enabling providers to offer confidential compute resources and earn rewards. This means that users requiring highly sensitive data processing for AI workloads, such as training on proprietary datasets or running inference on confidential inputs, can use decentralized compute nodes equipped with TEEs. The rofl marketplace is an example of this, as are projects like Cudos, io.net, Fluence, and others.
Second, DePIN apps can be integrated with TEEs. This means data provenance and integrity remain verifiable, sensitive operations happen in encrypted memory, and only privacy-preserving outputs get published. For instance, an app that incentivizes the aggregation of health data could do its processing entirely within a secure enclave. The raw sensor data serves as confidential input while the TEE guarantees that it’s never exposed in plaintext to the cloud provider, node operator, or even the DePIN's own infrastructure.
Real World Examples
DePINs are tackling infrastructure problems across a wide range of domains, from video processing to GPS accuracy to fractional ownership of physical assets. The scope reveals both the ambition and complexity of a crypto-native approach to building core infrastructure.
Take compute infrastructure as an example. Livepeer transforms idle GPUs into a video transcoding network, addressing the massive costs related to streaming/on-demand video. PinLink goes further, tokenizing hardware ownership through NFTs, enabling GPU owners to rent capacity while selling fractional stakes. They've tokenized access to Oasis nodes, letting users earn rewards from privacy-preserving infrastructure.
Then there’s location and mapping use cases. GEODNET crowdsources GPS base stations for centimeter-level accuracy, addressing the precision gap preventing widespread adoption of autonomous vehicles and precision agriculture. While Hivemapper mobilizes dashcam owners to create fresh street-level maps, challenging Google's monopoly with crowd-sourced data.
A final example is Diode, a project running a Zero Trust Network Architecture (ZTNA) that secures remote collaboration through a distributed network of nodes. Diode supports applications like secure communication, remote work, and data sharing. The privacy issue is handled via end-to-end encryption, with the recent collaboration with Oasis enabling integration of confidential smart contracts to further protect access controls and routing data.
Other privacy approaches vary by use case. Livepeer uses video encryption, and Hivemapper blurs identifying details. But most projects face the same tension: blockchain payments expose wallet addresses and transaction patterns, potentially compromising user identity.
DePIN: The Road Ahead
With its novel use of crypto incentives, DePIN can enhance resource utilization, efficiency, and spread the ownership of critical infrastructure to a bigger group of participants. DePIN excels when scaling infrastructure for a single provider is costly or cumbersome, when there are supply & demand inefficiencies, or when you can accelerate a cheaper end-state by bringing previously underused assets to full capacity.
Without question, DePIN represents one of crypto's most credible real-world applications. And the potential only increases as hardware continues to get better, faster, and cheaper. But two key issues stand in the way. One is the ongoing question of how to create tokenomic systems that are equitable and produce value over time. The other is how to handle privacy at scale.
While poster-child projects like Helium are leading the way, most DePINs are pre-PMF and rely on hybrid architectures where transparent crypto rails handle payments while other data remains centralized. These issues are well-known, and many teams are addressing them, but the path forward demands more than band-aids. If DePINs can't demonstrate that their systems are fundamentally more trustworthy, it's worth asking what's actually being achieved.



.png)